CAT CTF 2023 Digital Forensics writeup

In this post, I’ll be describing how I solved all Digital Forensics Challenges

its memory image and need suitable profile?
vol.py -f R4n.vmem imageinfo

FLAG: CATF{Win10x64_19041}

from description its need the parent process of the ransomware?
and extension after encrypt the data
i used pstree plugin to show all process

this the malware but we need check if we are right or not i used plugin procdump and upload it in virustotal

then ppid for R4n50m.exe is 3564 refer to explorer.exe
to get ext we have two method
filescanand show encrypted file- search about ransomware.dacic/clop

vol.py -f R4n.vmem windows.filescan | grep Desktop
FLAG: CATF{explorer.exe_Clop}
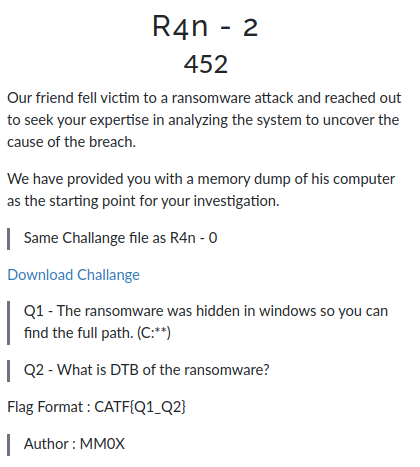
we have the name of malware R4n50m.exe
i used filescan to get all files and grep to get only R4n50m.exe path

now we have the path we need to get DTB
to get DTB we need use volshell
and we remember the pid of malware

FLAG: CATF{C:\Users\Work\AppData\Local\Temp\R4n50m.exe_0x45ebb000}

in here need Mitre ID and email of manager
note: all the ransomware after encrypt files leave a message contain some information such as email address to contact them
after dump it and upload it in hybrid-analysis

i used photorec to get the readme you can get it using strings two method are right
strings R4n.vmem| grep -i “Contact email” -A 10 -B 10

FLAG: CATF{T1027_managersmaers@tutanota.com}

in first i tried analysis it used oletools to show any malicious code or macros inside it

its clean

exiftool Targets.xlsx
we got the creator name and i used unzip to show files


FLAG: CATF{Th3–0b3l1sk_n!NjaTur7l5}

file is memory image from windows
after reading the description we knew it’s a developer this info will help us
- Q1 bitcoin wallet address, to get we have two method use strings or unpack the malware
- all of ransomware leave a message with some information like email to contact them and unique id for all victims and the bitcoin wallet
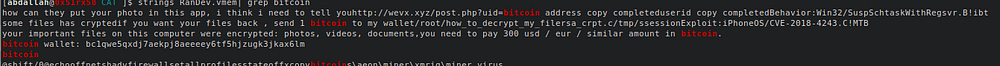
strings RanDev.vmem | grep bitcon
- A1: bc1qwe5qxdj7aekpj8aeeeey6tf5hjzugk3jkax6lm
now we need to get the ransomware
i used pstree to show all process

no process are suspicious but we remember its developer

vol.py -f RanDev.vmem windows.netscan
and the server was up and ports for mysql and web server
in first xamppis web server and important artifacts we can get from it
- web logs for access
- code of running web server

vol.py -f RanDev.vmem windows.filescan | grep xampp
we need dump the access.log and error.log to show what happen
we can do this using pid or address
vol.py -f RanDev.vmem windows.dumpfiles — virtaddr address

there are access for the php files we need dump it to show what inside it

vol.py -f RanDev.vmem windows.filescan | grep -E “\.php”
after get it we can now read content

its php code to check if POST request and username = user and password = password will run the malicious code to download the ransomware -> save it -> execute
if the if condition not true will redirect to login.php
after decode the base64 encode http://192.168.235.137/download/R.exe
http://192.168.235.137/download/R.exeurl for the ransomware- file name
R.exe - save it in
C:\Users\Work\Downloads\ execfunction to execute it
now we need to dump ransomware

vol.py -f RanDev.vmem windows.filescan | grep R.exe
after dump it just we need get sha256sum
FLAG: CATF{bc1qwe5qxdj7aekpj8aeeeey6tf5hjzugk3jkax6lm_d22aff59eae7201e6a4f82dbe99173c7103665beaa0860f81db7130f38c99a35_http://192.168.235.137/download/R.exe_exec}

all data we need inside the ransomware
after open it in ghidra

- A1 fake key
KRKTCUCXIZJESUSVNBBFCMDUIZKWOPJ5 - from function name we know its
xor encryption


- its contain the key and ext
- right key =
0x2c - ext =
.D7K - and we can solve it by other method to decrypt file run the malware in vm and will decrypt the
Tasks.txtbecause it xor encryption

FLAG: CATF{KRKTCUCXIZJESUSVNBBFCMDUIZKWOPJ5_.D7K_0x2c_17}
Finally i got first place






![[CyberDefenders Write-up] Web Investigation](https://miro.medium.com/v2/resize:fit:679/0*i1TwKK1pPpq0vjgn.png)

