In this post, I’ll be describing how I solved Digital Forensics Challenges
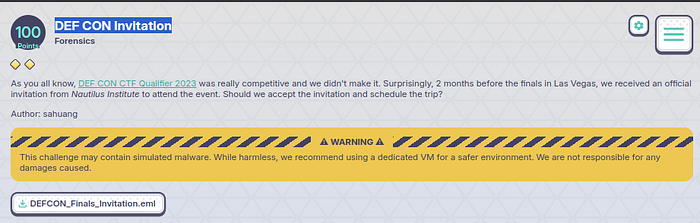
In the realm of digital forensics, every email holds the potential to unveil a story of intrigue and deception. Our journey begins with a seemingly innocuous .eml file that arrived in our inbox — a fabricated invitation to the prestigious DEFCON conference. What unfolds is a tale of investigative prowess, digital breadcrumbs, and the unmasking of a cunning ruse.
ok let’s analysis it

as we can see headers SPF is softfail and sender nautilus@nautilus.org

it’s attachment and filename -> dc31-invite.ics
we need decode it as base64 to see content

that link can be contain a lot of things

after click download it not a image :) its vbs code
As we scrutinized the attachments, our attention was seized by a VBScript file — an assembly of commands and functions that could either orchestrate legitimate processes or pave the way for cyber mayhem. In the realm of DFIR, such scripts are gateways to understanding the attacker’s methodologies and goals.
it 800 lines i will just focus in important points

Embedded within the script is the Replace function — a crucial tool that forms the linchpin of our analysis. This function acts as a transformative agent, reshaping the obfuscated strings into something potentially more meaningful. Our endeavor is to uncover the transformational power of these replacements, like discovering a cipher’s key.
Each occurrence of “IlllIllIIIllllIllII” within the script is replaced with a space character, thereby forming a sequence that appears less convoluted. This simple act of substitution grants us a glimpse into the script’s underlying logic, hinting at patterns and interactions that may hold the answer to its purpose.
68 74 74 70 73 3a 2f 2f 64 6f 77 6e 6c 6f 61 64 31 36 34 37 2e 6d 65 64 69 61 66 69 72 65 2e 63 6f 6d 2f 6c 31 38 38 75 32 64 35 33 32 71 67 33 66 4f 6f 4c 70 69 6c 63 49 38 39 70 30 5f 68 34 45 30 63 47 4c 6a 6b 5f 75 76 42 55 69 61 67 37 45 5f 72 4d 5a 2d 48 35 2d 6d 65 39 4b 72 39 53 51 4c 56 51 61 4b 53 69 4b 63 45 76 4a 4f 2d 45 6b 66 54 53 55 71 57 6c 72 4e 36 53 7a 58 67 49 30 4c 59 42 68 2d 46 35 65 6d 34 49 41 34 69 58 33 74 4f 49 47 68 30 45 6a 34 36 47 6c 77 76 4c 4f 66 54 38 70 7a 76 75 79 39 31 55 74 65 6a 31 72 32 49 30 6a 67 37 59 73 55 4e 63 73 73 50 74 65 64 35 30 38 64 73 6b 57 52 70 6b 41 49 2f 79 65 61 35 33 35 68 76 67 70 33 32 76 6d 76 2f 64 65 66 63 6f 6e 2d 66 6c 61 67 2e 70 6e 67 2e 58 4f 52 65 64Within the hex-encoded sequence, a specific operation takes center stage — downloading the file named “defcon-flag.png.XORed.” This enigmatic artifact holds intrigue within its name, suggesting a connection to flag file and a cryptographic operation. The XOR operation often serves as a safeguard, masking the content behind a veil of encryption.

In this digital symphony, two main actors grace the stage. First, there’s xHttp, a Microsoft XMLHTTP agent — akin to a digital retriever — sent on a mission to fetch encrypted data from a remote vault. Then, enter bStrm, an Adodb.Stream conductor, ready to catch and elegantly hold this retrieved treasure.
As the symphony commences, xHttp takes the spotlight and is dispatched to a remote destination, armed with the “GET” command. Its objective? To seize the encrypted treasure concealed within the mysterious OwOwO(ewkjunfw). This act initiates our journey to unravel the mysteries shrouded within “defcon-flag.png.XORed.”
The Transformation: bStrm’s Elegant Performance:
Next, bStrm takes center stage, its gates flung open to welcome the obtained treasure. Guided by the virtuosity of Adodb.Stream, the script gracefully transposes its role — decrypting, shifting, and molding the captured artifact. This transformation showcases the script’s mastery over data manipulation, paving the way for further examination.
we need replace ###############_### to z, and reverse it

it will execute this code and we need show what will execute i replaced Execute to Msgbox to print the code

in first will call http://20.106.250.46/sendUserData
and POST request and Content-type json
and will send username and value for username

now we have xor key to decrypt the defcon-flag.png.XORed

The rest of the challenges i will add it later







